For years, Indicators of Compromise have been the backbone of threat detection. IP addresses, domains, file hashes — they were easy to share, easy to block, and easy to explain. If something malicious appeared on a list, defenses reacted. For a long time, this approach worked well enough.
Today, it no longer does.
Modern attacks are not failing because defenders lack IOCs. They fail because IOCs arrive too late, change too quickly, or never appear at all. What once felt like solid intelligence has slowly turned into historical data.
When Detection Becomes Reactive by Design
IOC-driven detection is, by nature, reactive. An indicator only exists after something bad has already happened somewhere else. By the time it is shared, ingested into a SIEM, and deployed across security controls, the attacker has often moved on.
In real incident investigations, this pattern appears repeatedly. Analysts discover that an IP was malicious — but only after it stopped being used. A domain is flagged — after it has already served its purpose. Hashes are blocked — long after payloads were rotated or abandoned.
Threat actors understand this delay and design their operations around it.
Attackers Don’t Need Stable Infrastructure Anymore
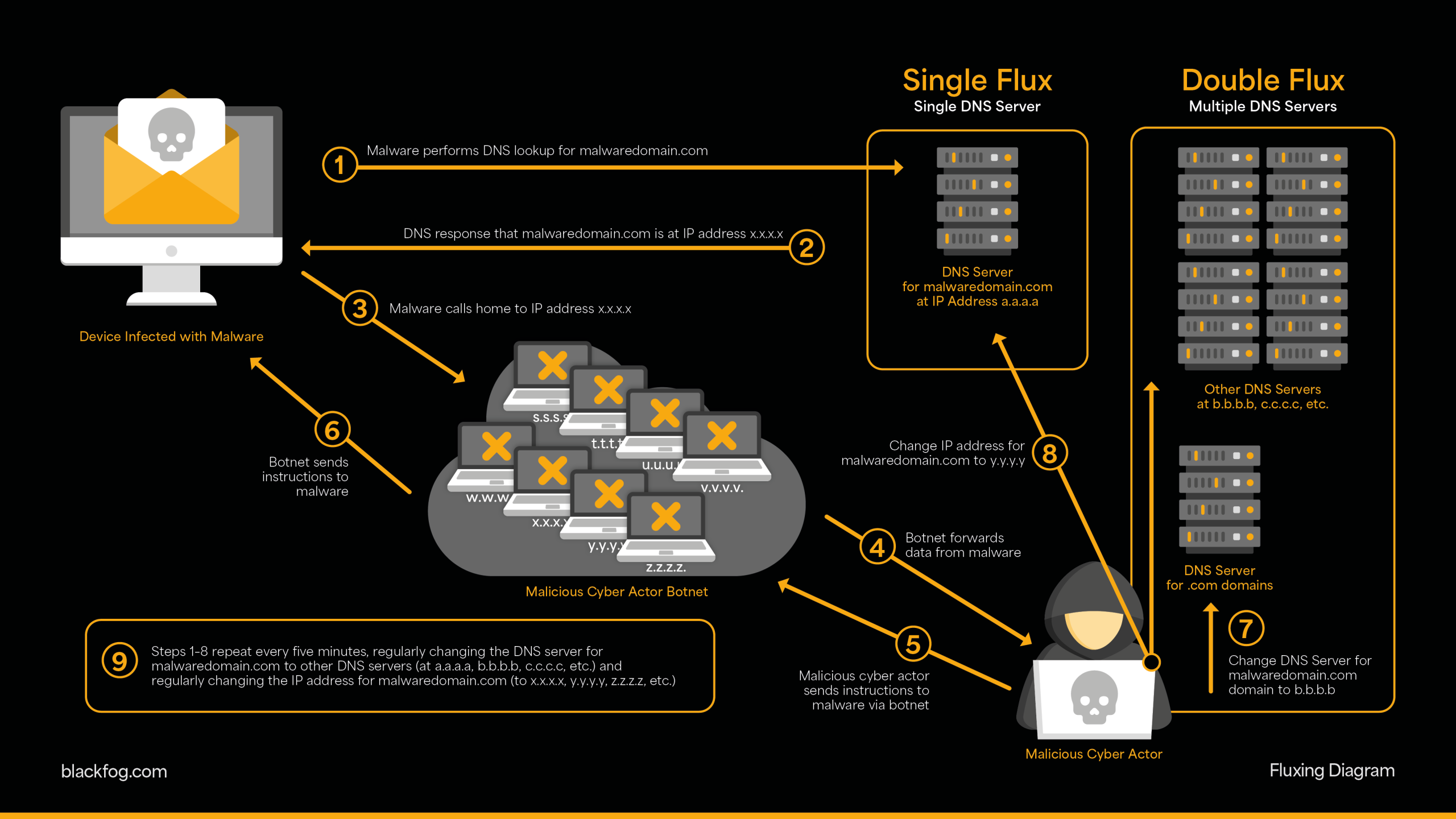
One of the biggest shifts in recent years is how short-lived attack infrastructure has become. Domains exist for hours instead of weeks. IP addresses rotate constantly. Payloads are rebuilt on demand. In some cases, attackers rely entirely on legitimate platforms, making traditional indicators meaningless.
This creates a fundamental problem for IOC-based detection. Indicators are no longer persistent enough to be reliable. Blocking them feels effective, but often has no real impact on the attack itself. The infrastructure is disposable, and the attacker is already operating elsewhere.
Detection based purely on IOCs begins to resemble chasing shadows.
What Gets Missed When We Focus on IOCs
When teams focus heavily on indicators, they often miss what actually matters: behavior. Credential abuse, unusual access patterns, abnormal API usage, and subtle shifts in user activity rarely come with clean IOCs attached. These attacks look legitimate because, technically, they are using allowed paths.
In many breaches, there are no malicious domains, no known bad hashes, and no clear signatures. The compromise lives entirely within expected system behavior. IOC-driven tools remain silent, while the attacker operates comfortably inside the environment.
The failure here is not a lack of data, but a lack of context.
This Is Not the End of Intelligence — Just the Old Model
The decline of IOC-driven detection does not mean threat intelligence has lost its value. It means the role of intelligence has changed. Indicators still matter, but they are no longer the center of detection. They work best when combined with behavioral analysis, identity context, and an understanding of how systems are actually used.
Modern detection is less about blocking known bad things and more about recognizing when something “normal” starts behaving differently. That shift requires moving from lists to patterns, from feeds to context.
Conclusion
IOC-driven detection is not broken — it is simply no longer sufficient on its own. Threat actors have adapted to its limitations, and many modern attacks are built specifically to avoid producing useful indicators. As long as defenders rely on yesterday’s signals to detect today’s behavior, detection will remain one step behind.
The future of detection is not faster IOC feeds. It is understanding what does not belong — even when nothing obviously malicious appears.
